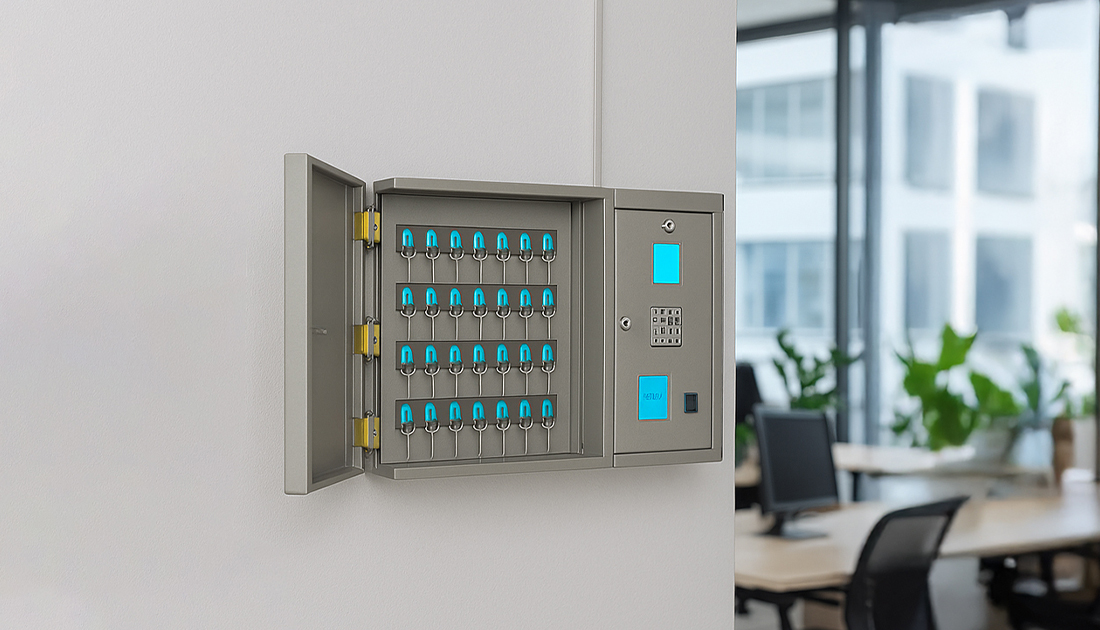
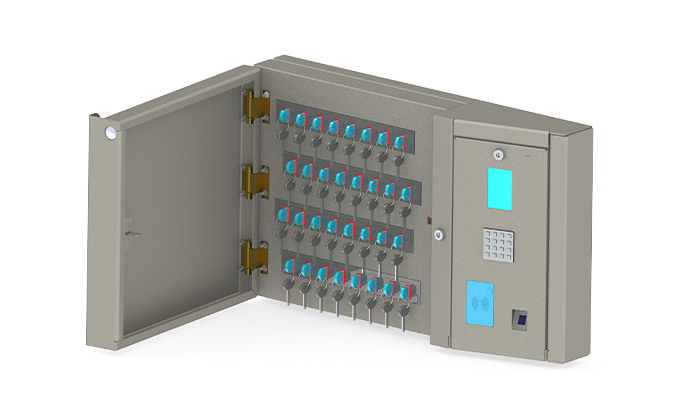
Access Authentication
Multi-Level User Verification : Establish a clear and logical structure that mirrors your organization’s operational setup, whether you operate locally or globally.
Two-Factor Security : Map For high-security environments, dual authentication (e.g., RFID + Fingerprint) can be enabled to prevent unauthorized access.